
IoT Gateway Security: A Complete Guide for Secure Deployments

Blog Summary:
IoT gateways play a central role in managing device communication, data processing, and edge intelligence. Their critical position makes them a prime target for cyber threats if not properly secured. This blog explores key gateway functions, common security risks, essential protection features, and best practices for resilient deployments. With the right strategy and expert support from BigDataCentric, organizations can build scalable, secure IoT environments that support long-term growth.
IoT gateways play a critical role in connecting devices, networks, and cloud platforms, acting as the central point where data is aggregated, processed, and transmitted. As these gateways handle sensitive device data and control communication across multiple protocols, their exposure makes them a frequent target for cyber threats.
With connected systems now widely used in industrial, healthcare, logistics, and smart infrastructure environments, a single compromised gateway can impact entire networks.
This is why IoT gateway security has become essential for protecting data integrity, maintaining operational continuity, and preventing unauthorized access across distributed environments.
Since gateways often operate in remote or unattended locations and manage diverse device ecosystems, they require security measures that go beyond traditional IT controls.
Addressing authentication, encryption, firmware protection, and access control early helps organizations reduce risk while supporting scalable and reliable connected deployments.
What is IoT Gateway Security?
IoT gateway security refers to the set of technologies, controls, and practices used to protect gateways that connect edge devices with networks, data centers, or cloud platforms.
These gateways act as intermediaries, handling device communication, data filtering, and protocol translation, which makes them a critical point for enforcing security controls within connected ecosystems.
A secure gateway ensures that only authorized devices and users can access the network, data transmitted between endpoints remains protected, and malicious activity is detected before it spreads.
This involves securing both the hardware and software layers of gateway devices, including operating systems, firmware, communication channels, and management interfaces.
At a broader level, IoT gateway security helps maintain trust across connected environments by preventing data leaks, unauthorized control, and service disruptions.
When implemented correctly, it forms the backbone of a secure IoT deployment, enabling organizations to scale device networks while maintaining visibility, control, and resilience against cyber threats.
Role of IoT Gateways in Modern IoT Architecture
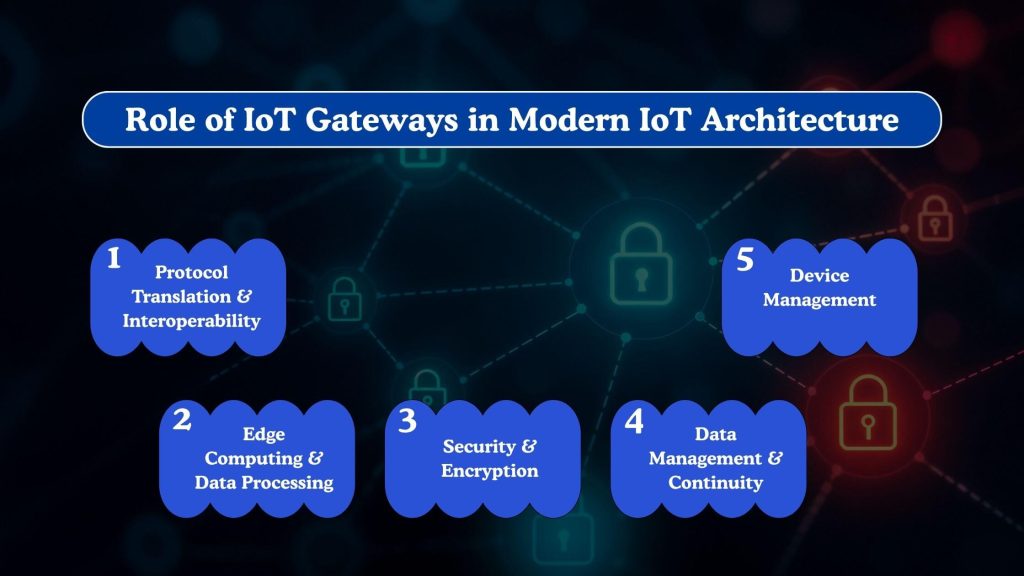
IoT gateways act as a central control layer between edge devices and backend systems, enabling reliable communication, local intelligence, and secure data exchange. In modern big data architectures, they help manage device diversity, reduce network dependency, and maintain operational stability across distributed environments.
Protocol Translation & Interoperability
Connected environments often rely on multiple communication protocols such as MQTT, CoAP, HTTP, Modbus, or proprietary standards. IoT gateways translate these protocols into a common format, allowing different devices and platforms to communicate seamlessly.
This interoperability is essential for integrating heterogeneous IoT gateway devices into a unified system without redesigning the existing data infrastructure.
Edge Computing & Data Processing
Gateways support edge computing by processing data locally before sending it to centralized systems. This reduces latency, minimizes bandwidth usage, and enables faster decision-making for time-sensitive applications.
Local filtering and aggregation also help ensure that only relevant data is transmitted, improving performance and system efficiency.
Security & Encryption
Gateways serve as a frontline security layer by enforcing encryption, authentication, and access control policies. They help secure communication between devices and networks, ensuring data confidentiality and integrity.
By acting as a controlled entry point, gateways play a vital role in maintaining a secure iot gateway environment and limiting unauthorized access.
Data Management & Continuity
IoT gateways manage data flow during network disruptions by buffering, storing, and forwarding information once connectivity is restored. This approach ensures operational continuity while strengthening data security and preventing loss under unstable network conditions. Effective handling also supports reliable analytics and long-term system monitoring.
Device Management
IoT Gateways simplify device onboarding, monitoring, and configuration across large deployments. They enable centralized control over firmware updates, device status, and connectivity health.
This capability is crucial for maintaining consistent performance and reducing operational overhead as connected ecosystems scale.
Why IoT Gateways are a Prime Target for Cyberattacks?
The location of IoT gateways between edge devices and core systems makes them a desirable target for hackers. A successful compromise can provide access to device data, control traffic flow, or disrupt operations across an entire deployment.
Their constant connectivity, exposure to external networks, and role in managing multiple devices significantly increase their attack surface.
Single Point of Failure
Gateways often act as centralized hubs for device communication and data aggregation. If compromised, attackers can intercept data, manipulate device behavior, or shut down services altogether. This concentration of control makes gateways a high-value target, especially in large-scale or industrial deployments.
Poor Patching & Firmware Management
Many gateways run outdated firmware due to manual update processes or limited maintenance windows. Delayed patching leaves known vulnerabilities unaddressed, giving attackers an opportunity to exploit weaknesses in operating systems, drivers, or embedded services.
Botnet Recruitment
Compromised gateways are frequently used as entry points for botnet infections. Once controlled, they can be leveraged to spread malware to connected devices or participate in large-scale attacks, such as distributed denial-of-service campaigns, without immediate detection.
Unencrypted Data Transmission
Gateways that transmit data without proper encryption expose sensitive information to interception and tampering. Unsecured communication channels allow attackers to eavesdrop, inject malicious payloads, or manipulate device commands, undermining the reliability of the entire connected environment.
Don’t Let Weak Security Expose Your IoT Network
Strengthen your IoT gateway security to ensure seamless, safe data flow and connected systems.
Common Security Threats Affecting IoT Gateways
IoT gateways face a wide range of security threats due to their constant connectivity, interaction with multiple devices, and exposure to both internal and external networks.
These threats can compromise data confidentiality, disrupt operations, and weaken the overall security posture of connected environments if not addressed proactively:
Unauthorized Access and Weak Authentication
Weak or default credentials, lack of multi-factor authentication, and improper access controls make gateways vulnerable to unauthorized access. Attackers can exploit these gaps to gain administrative privileges, alter configurations, or control connected devices without detection.
Insecure Communication & Data Transmission
When data is transmitted without secure protocols, it becomes susceptible to interception and manipulation. Insecure communication channels allow attackers to perform man-in-the-middle attacks, inject malicious commands, or extract sensitive information as data moves between devices and backend systems.
Firmware and Software Vulnerabilities
Gateways often rely on embedded operating systems and third-party components that may contain unpatched vulnerabilities. Exploiting these flaws enables attackers to execute malicious code, escalate privileges, or establish persistent access within the gateway environment.
Insecure Network Services
Unnecessary open ports, exposed APIs, and misconfigured services increase the attack surface of gateways. These weaknesses can be exploited to scan networks, launch brute-force attacks, or bypass perimeter defenses within a secure iot network.
Ransomware
Ransomware attacks targeting gateways can encrypt critical configurations or disrupt device communication. In operational environments, this can halt production processes, cause downtime, and force organizations into costly recovery efforts.
Botnets and Distributed Denial of Service (DDoS)
Compromised gateways are often recruited into botnets and used to launch DDoS attacks. Their processing power and network access make them effective tools for overwhelming targeted systems while remaining difficult to trace back to the source.
Core Security Features Every IoT Gateway Should Have
To protect connected environments from evolving cyber threats, gateways must be built with security as a core capability rather than an afterthought.
Strong security features help reduce exposure, prevent unauthorized access, and maintain control over data and devices throughout the gateway lifecycle.
Device and Gateway Identity Management
Every gateway and connected device should have a unique, verifiable identity. Identity management ensures that only trusted devices can connect to and communicate within the network.
This includes secure provisioning, certificate-based authentication, and role-based access controls that prevent unauthorized entities from impersonating legitimate devices.
Network Security and Firewall
Gateways should include built-in network security controls such as firewalls, traffic filtering, and intrusion detection mechanisms.
These features help monitor incoming and outgoing traffic, block suspicious activity, and restrict access to only approved communication paths. Proper network segmentation also limits the lateral movement of threats across connected systems.
Secure Data Transmission (Encryption)
Encryption is essential to protect data as it moves between devices, gateways, and backend systems. Secure communication protocols prevent data interception, tampering, and eavesdropping.
By enforcing encrypted channels, gateways help maintain data confidentiality and integrity across distributed environments.
Secure Remote Management (OTA Updates)
Secure remote management enables administrators to monitor, configure, and update gateways without physical access. Over-the-air updates allow timely deployment of security patches and feature enhancements while ensuring update authenticity and integrity. This capability is critical for maintaining long-term protection in large-scale deployments.
Best Practices for Strengthening IoT Gateway Security
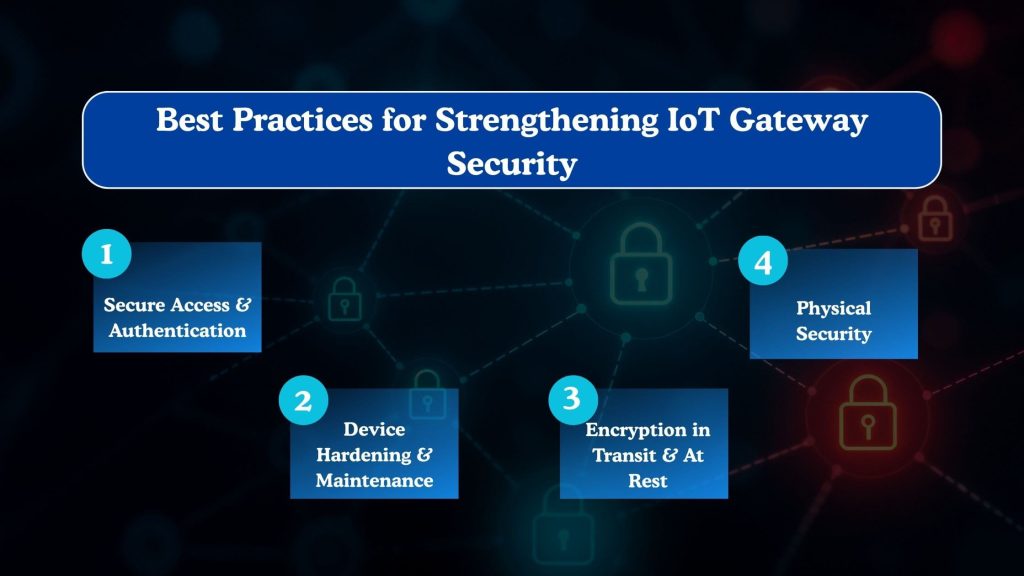
Securing gateways requires a combination of technical controls, operational discipline, and ongoing monitoring. Applying proven best practices helps reduce vulnerabilities, limit attack surfaces, and maintain reliable operations across connected environments.
Secure Access and Authentication
Strong authentication mechanisms are essential to prevent unauthorized access. This includes disabling default credentials, enforcing strong password policies, and using certificate-based or multi-factor authentication for administrative access.
Limiting privileges based on roles further reduces the risk of misuse or compromise.
Device Hardening and Maintenance
Gateways should be hardened by disabling unnecessary services, closing unused ports, and removing unused applications.
Regular maintenance, including firmware updates and vulnerability patching, helps eliminate known security gaps and ensures the gateway software remains resilient against emerging threats.
Encryption in Transit and At Rest
Encrypting data both during transmission and while stored on the gateway protects sensitive information from interception and unauthorized access.
Secure protocols and trusted cryptographic standards help maintain data integrity, even if network traffic is monitored or storage media is accessed.
Physical Security
Since gateways are often deployed in remote or industrial locations, physical protection is critical. Secure enclosures, tamper detection mechanisms, and controlled access to hardware ports help prevent physical manipulation, device theft, or unauthorized configuration changes.
IoT Gateway Security in Edge and Industrial Environments
Gateways deployed in edge and industrial settings operate under conditions that differ significantly from traditional IT environments. They often support mission-critical operations, run continuously, and function in remote or physically exposed locations.
These factors demand a stronger and more specialized security approach to protect systems from disruption and data compromise.
Software and Operational Security
In edge environments, gateways must be secured at the operating system and application levels. This includes enforcing secure boot processes, restricting software execution, and continuously monitoring system behavior for anomalies.
Operational controls such as logging, alerting, and remote monitoring help detect suspicious activity early and reduce response time when incidents occur. Consistent operational security ensures gateways remain resilient without impacting real-time performance.
Industrial-Specific Security Considerations
Industrial deployments introduce additional risks due to legacy systems, proprietary protocols, and strict uptime requirements. Gateways often bridge older operational technology with modern networks, increasing exposure if controls are not properly enforced.
Security measures must be carefully implemented to avoid disrupting processes while still protecting against unauthorized access, lateral movement, and protocol-level attacks.
Hardware-Based Security (Root of Trust)
Hardware-based security mechanisms provide a strong foundation for protecting gateways in hostile environments. A hardware root of trust ensures that only verified firmware and software can run on the device, preventing tampering during boot or runtime.
Secure elements and trusted data platform modules also protect cryptographic keys and credentials, strengthening overall trust in the gateway’s operation.
How Businesses Can Implement a Scalable IoT Gateway Security Strategy?
As IoT deployments grow, security strategies must scale without increasing complexity or operational overhead. A structured approach helps organizations maintain consistent protection across expanding gateway and device ecosystems while supporting long-term business objectives.
Strategy for Scalability
Scalable security starts with standardized architectures and policies that can be applied across deployments. Using modular security frameworks allows organizations to onboard new gateways and devices without redesigning controls.
This approach supports consistent enforcement while adapting to changing network sizes and use cases.
Automated Lifecycle Management
Automation plays a key role in maintaining security at scale. Automated provisioning, monitoring, and patch management reduce manual effort and ensure gateways remain up to date throughout their lifecycle.
Centralized management tools also improve visibility and help teams respond quickly to vulnerabilities or configuration issues.
Device Identity and Access Management
Strong identity and access management ensure that only trusted devices and users can interact with gateways.
Unique device identities, certificate-based authentication, and role-based access controls help prevent unauthorized connections as the network grows, supporting a secure IoT gateway ecosystem.
Foundational Security Hardening
Foundational hardening includes secure configurations, minimal service exposure, and continuous vulnerability assessment.
Establishing these baseline controls early ensures new gateways inherit strong security settings by default, reducing risk as deployments scale and evolve.
Looking for Expert Support on IoT Gateway Security?
Specialized guidance helps align gateway security with enterprise, edge, and industrial IoT requirements.
Conclusion
Securing IoT gateways is no longer a technical afterthought—it is a business-critical requirement. As gateways control device communication, data flow, and edge intelligence, even a minor security gap can expose entire connected environments to operational disruption and data compromise.
A well-structured approach to IoT gateway security helps organizations protect sensitive data, maintain uptime, and build long-term trust across connected systems.
For businesses navigating complex, large-scale deployments, working with experienced technology partners is essential. BigDataCentric supports organizations in designing and implementing secure, scalable IoT architectures by combining deep expertise in connected systems, data platforms, and enterprise-grade security practices.
From strengthening gateway-level controls to aligning security with broader analytics and digital transformation initiatives, the focus remains on building resilient and future-ready IoT ecosystems.
By adopting the right security features, following proven best practices, and planning for scalability from the start, organizations can confidently expand their IoT initiatives without increasing risk.
A strong gateway security foundation ensures connected environments remain reliable, compliant, and ready to support evolving business needs.
FAQs
-
Does the IoT gateway provide security for the network?
Yes, an IoT gateway helps secure the network by controlling device access, filtering traffic, and encrypting data between devices and backend systems. It acts as a security enforcement point at the edge.
-
Is IoT gateway security critical for industrial IoT?
Yes, it is critical in industrial IoT because gateways connect operational systems with enterprise networks. A compromised gateway can disrupt operations, cause downtime, or expose sensitive industrial data.
-
Can IoT gateways support secure remote access?
Yes, IoT gateways can support secure remote access using encrypted communication, authentication controls, and secure management interfaces, allowing administrators to manage devices safely from remote locations.
-
Which security protocol is commonly used in IoT devices?
The commonly used security protocols include TLS and DTLS, which secure data transmission by encrypting communication between devices, gateways, and servers.
-
How can we secure IoT devices?
IoT devices can be secured by using strong authentication, encrypted communication, regular firmware updates, and restricting network access to only trusted systems.

About Author
Jayanti Katariya is the CEO of BigDataCentric, a leading provider of AI, machine learning, data science, and business intelligence solutions. With 18+ years of industry experience, he has been at the forefront of helping businesses unlock growth through data-driven insights. Passionate about developing creative technology solutions from a young age, he pursued an engineering degree to further this interest. Under his leadership, BigDataCentric delivers tailored AI and analytics solutions to optimize business processes. His expertise drives innovation in data science, enabling organizations to make smarter, data-backed decisions.
Table of Contents
ToggleHere's what you will get after submitting your project details:
- A strict non-disclosure policy.
- Get in discuss with our experts.
- Get a free consultation.
- Turn your idea into an exceptional app.
- Suggestions on revenue models & planning.
- No obligation proposal.
- Action plan to start your project.
- We respond to you within 8 hours.
- Detailed articulate email updates within 24 hours.
Our Offices
USA
500 N Michigan Avenue, #600,Chicago IL 60611




